With so many new and emerging threats to worry about in today’s cybersecurity landscape, it’s no wonder that some businesses and employees might be operating from a knowledge deficit regarding network security. We’re here to change that with a quick overview of the three biggest overarching threats your business must face and prepare for.
Home
About Us
IT Services
Understanding IT
- Understanding General Data Protection Regulation Compliance
- Understanding Automation
- Understanding Ransomware
- Understanding Shadow IT
- Understanding Your Virtual Identity
- Understanding the Modern Office
- IT Threat Glossary
- Understanding Business Continuity
- Windows Server 2003: End of Life
- Understanding the Internet of Things
- Understanding Network Security
- Understanding SOX
- Understanding BYOD
- Understanding PCI DSS
- Windows XP End of Life
- Understanding HIPAA
- Cloud Computing
News
Blog
Support
Contact Us
(713) 979-2090
- Register
- Login
Zinc Blog
Managing a business poses considerable challenges, with a myriad of tasks demanding attention daily just to sustain the status quo. If you want to have a workforce that is not just present but genuinely invested in the enterprise, you will need to actively do more than just go through the motions. The question then becomes: How can one cultivate such dedication? This month, we will take a look at that very question.
Scams using online retail giant Amazon have become more frequent around the holidays as online purchases tick up. Most of these scams come in the way of impersonation scams. With the holidays upon us, we thought we’d go through what kind of Amazon scams you should look for and how to avoid being a victim.
With the holiday season upon us and online shopping surging, instances of scams targeting the popular e-commerce platform Amazon have become increasingly common. The majority of these scams involve impersonation tactics, posing a significant threat to unsuspecting users. With the festive season underway, it's crucial to be aware of the types of Amazon scams prevalent and take measures to avoid falling victim to them.
The Internet allows online transactions to take place, but they must be properly protected so that hackers and cybercriminals don’t make off with your sensitive data. Here are some simple ways you can ensure that your business is protecting its online transactions.
Cyberattacks are horrifically dangerous to any business, especially for small ones that might not have the resources to protect themselves with top-dollar solutions or preventative solutions to bounce back afterward. Today, we want to explore what really causes cyberattacks and how even slight changes to behaviors and situations can be indicative of danger.
Using the right technology can streamline operations, enhance customer engagement, and boost overall productivity. Despite its potential benefits, many small businesses often make significant mistakes when it comes to technology implementation. Let’s explore some of the biggest technology blunders small businesses make and how to avoid them.
Data is commonly regarded as one of a business’ most valuable resources. As such, it is critical that you protect it from threats of all kinds, including data leaks. Data leaks are nothing to take lightly, as their impacts range from a serious hit to your business’ reputation to an equally serious hit to your business’ finances. Obviously, this is something to be avoided, so let’s discuss how you can do so.
Today’s business leans on collaboration more than ever. Employees that work together efficiently and effectively can streamline processes and create a lot of positive momentum for a business that includes enhancing productivity and fostering innovation. Let’s go through a few variables that fuel solid collaboration.
We’ve all found ourselves in a pickle due to a dead smartphone battery, and if not, you’ve been living with a charger perpetually on your person. What is it that kills a smartphone’s battery so quickly?
As it turns out, a lot of things impact your smartphone’s capability to hold and maintain a charge over time. Let’s run through the list of factors that you could encounter, and how you can address them.
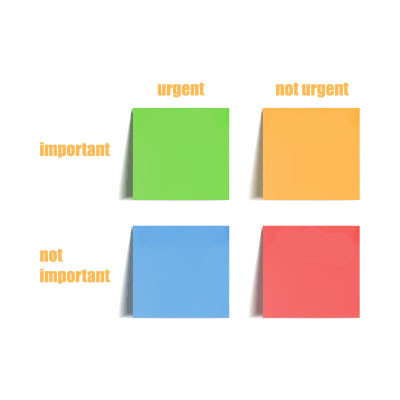
The modern worker has a lot of challenges and one of them is a laundry list of tasks to accomplish. For this reason, it’s best to have a plan for tackling your to-do list. One of the most effective ways to prioritize tasks is through what is called the Eisenhower Matrix. Inspired by a speech given by the former President of the United States and the Supreme Commander of the Allied Expeditionary Force in World War II, the Eisenhower Matrix simplifies complex task lists to make getting through them more effective. Let’s take a look at how it works.
The IT infrastructure of any business can be complicated, especially if you’re going about things the right way. In fact, managing your technology is, more often than not, a full-time job that needs to be fulfilled in order to be done appropriately. Let’s go over some of the key parts of managing and maintaining a business IT infrastructure, and while we cover these tasks, ask yourself if you’re 100% confident that they are happening for your business.
Look, we know that thinking about disasters can be a nerve-wracking experience, but you need to acknowledge that your organization is constantly in danger of becoming subverted by challenges outside your control. While you might not be able to stop a disaster from striking, you can be prepared for when it does strike, as well as how you respond to it. Let’s go over some of the methods you can use to ensure you have a plan in place.
For the growing business, doing the right things to secure your network and data is a constantly evolving situation. For larger businesses, they tend to approach the situation with a different perspective. They plan out the whole process. This is what is called enterprise security. Let’s take a look at what enterprise security entails and how the little guy can benefit from doing things like larger companies do them.
If you’re anything like me, you’ve always got a thought in the back of your head regarding your business and how you can make it more productive. While there are a lot of different ways you can do so, we wanted to focus on one that might not be the first to come to mind: communicate more.
Cybersecurity has never been more important. There are millions of scams sent out every day that are ultimately targeting you and your employees’ password-secured accounts. Today, we are going to give you some tips on how to create passwords that work best to protect your data and information systems.
Phishing is a word that has a couple of different meanings, depending on the spelling and context. Fishing, like the act of sitting down with a pole and trying to catch a fish, can be a relaxing, leisurely activity. Phishing, with a “ph,” is anything but that, and it can be a tiring and scary situation to navigate—particularly if you or one of your employees have fallen victim to an attack.
Last week, we went through why training is such a crucial part of your business’ cybersecurity process. This week we will turn our attention to some of the tools and other strategies that your organization should be using to mitigate security threats.
Admit it, you don’t know all that much about cybersecurity. In this blog, we spend a lot of time discussing security issues. After all, today there are more threats than ever and many different types of problems that IT administrators, business decision-makers, and even individual employees have to deal with. Over the next two weeks, we have decided to discuss the reality of cybersecurity and what you need to know to get out in front of it.
It’s not uncommon for an employee to hold a second job outside of your office, whether it’s a side gig that they are trying to turn into a passion project or a side hustle just to make ends meet or put away a little extra money every month. Workers holding multiple jobs is certainly not unheard of—if anything it’s more common than ever, thanks to the remote work surge. How does this phenomenon impact your organization?