Home
About Us
IT Services
Understanding IT
- Understanding General Data Protection Regulation Compliance
- Understanding Automation
- Understanding Ransomware
- Understanding Shadow IT
- Understanding Your Virtual Identity
- Understanding the Modern Office
- IT Threat Glossary
- Understanding Business Continuity
- Understanding the Internet of Things
- Understanding Network Security
- Understanding SOX
- Understanding BYOD
- Understanding PCI DSS
- Windows XP End of Life
- Understanding HIPAA
- Cloud Computing
News
Blog
Support
Contact Us
(713) 979-2090

- Home
- About Us
- IT Services
- Understanding IT
- Understanding General Data Protection Regulation Compliance
- Understanding Automation
- Understanding Ransomware
- Understanding Shadow IT
- Understanding Your Virtual Identity
- Understanding the Modern Office
- IT Threat Glossary
- Understanding Business Continuity
- Understanding the Internet of Things
- Understanding Network Security
- Understanding SOX
- Understanding BYOD
- Understanding PCI DSS
- Windows XP End of Life
- Understanding HIPAA
- Cloud Computing
- News
- Blog
- Support
- Contact Us
- (713) 979-2090
- Home
- About Us
- IT Services
- Understanding IT
- Understanding General Data Protection Regulation Compliance
- Understanding Automation
- Understanding Ransomware
- Understanding Shadow IT
- Understanding Your Virtual Identity
- Understanding the Modern Office
- IT Threat Glossary
- Understanding Business Continuity
- Understanding the Internet of Things
- Understanding Network Security
- Understanding SOX
- Understanding BYOD
- Understanding PCI DSS
- Windows XP End of Life
- Understanding HIPAA
- Cloud Computing
- News
- Blog
- Support
- Contact Us
- (713) 979-2090
- Register
- Login
Zinc Blog
Here’s How Fast Your Password Can Be Cracked
Weak passwords are one of the leading causes of cybercrime, identity theft, and data breaches. Sure, it’s easy to say it, but this time we wanted to demonstrate just how easy it is to crack a wimpy password.
How Does One Crack a Password?
Hackers and cybercriminals have sophisticated tools to aid them. On top of that, they have plenty of useful knowledge on how the general public conducts themselves online.
Passwords, in particular, are a game of statistics. There are a handful of commonly used passwords that a cybercriminal can try first. These include things like the following:
- 123456789
- guest
- qwerty
- password
- a1b2c3
These are among the most commonly used passwords in the world. Trying variations of these, or simply sticking an exclamation point or two on the end of them have a chance of getting into an account. In fact, it’s likely that somewhere between 10 and 20 percent of all accounts use a common password similar to this.
If we put ourselves in the shoes of a cybercriminal, or someone who just wants to be mischievous, then we can take that knowledge and optimize our approach for getting into any account.
We invest in a password-cracking tool. This might sound complicated, but all this kind of tool needs to do is produce a massive list of words and strings of characters. Basically, it runs through every word in the dictionary first in a few moments, and then starts sifting through variations and different combinations of letters, numbers, and symbols, starting with smaller strings of characters first.
Okay, maybe I made it seem complicated.
Imagine trying to get into your neighbor’s garage. They have a pin pad with the numbers 0-9 and an “enter” key on it. If you wanted to get into their garage, you would just need to try every single possible combination of numbers until you found the right one.
Just by law of averages and some educated guessing, you can assume that the pin for the garage is probably 4 or 6 digits, so you start with four.
You try the following:
- 0000
- 0001
- 0002
- 0003
And you keep going until you’ve reached 9999, or the door opens.
If the door doesn’t open, you try every 6-digit option. That’s 000000 through 999999. That will take you much longer to do. By now, your neighbor is probably outside in their slippers asking you to please stop, and the next time you want to borrow their hedge trimmer, you can just ask.
Notice how much more time you need to spend with just two additional digits. It went from 10 thousand combinations to a million.
Instead of a 10-digit pin pad, if your neighbor’s garage had a full-sized keyboard, suddenly the potential combinations would increase exponentially. You simply wouldn’t be able to sit there and try every conceivable combination in your lifetime.
But a computer could, and a computer could do it very quickly.
That’s how a password-cracking tool works.
How Long Does it Take to Crack a Password?
Considering the fact that most cybercriminals are going to utilize tools that try the most common variations first, it could be instantaneous. Smaller, shorter, weaker passwords will only take a split-second to try. These tools can run through tens of millions of combinations in under a second.
It certainly depends on the hardware, so we’re basing our numbers on a decently powerful laptop. Here’s how quickly a password can be cracked based on the number of characters in it, and based on the complexity:
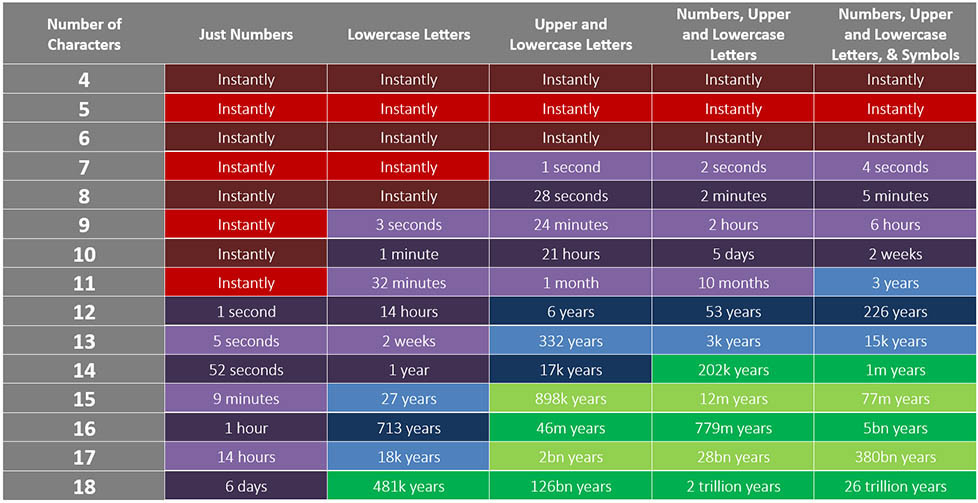
So you can see that weaker passwords can be cracked instantly, or within a few seconds or minutes. Once passwords have more characters and more complexity, it becomes *virtually* impossible to crack within someone’s lifetime.
I say virtually, because if your password is long and complex, but it’s just a common variation that can be guessed or a variation that might be attempted early on, then it won’t take nearly as long. The password “Password12345!” might seem complex and long, and according to the chart would take a million years to crack, but since it’s just using some of the most commonplace password trends, it’s considered extremely weak.
This is why strong, unique passwords are so important. You should never use the same password twice, and you should always use passwords that are long, complex, and don’t have guessable information in them (like birthdays, pet names, and other things like that).
And keep in mind, this is just using a commonly available tool on a commonly available laptop—more industrious cybercriminals might have access to more resources, such as botnets and cloud computing resources, and more advanced tools that can brute force password combinations at speeds hundreds or thousands of times faster.
In other words, always, ALWAYS use strong passwords!
About the author
Zinc has been serving the Texas area since 2017, providing IT Support such as technical helpdesk support, computer support, and consulting to small and medium-sized businesses.
- You are here:
- Home /
- Blog /
- Zinc IT Team /
- VoIP is the MVP of Business Communications

Comments